- Chinese-associated hackers are doubling down on their efforts in the interest of Beijing’s silicon self-sufficiency by sabotaging Taiwan’s semiconductor industry and infiltrating U.S.military bases in the form of cyber attacks to steal intellectual property and confidential data.
- A team of four hacking groups, i.e., UNK_ColtCentury, UNK_FistBump, UNK_DropPitch, and UNK_SparkyCarp have been named for targeting at least 15-20 organizations worldwide, ranging from small-scale vendors (weak links in the supply chain) to major global businesses, including the manipulation of analysts at U.S.-based international bank.
- China’s $150 billion attempt for self-subsistence in the semiconductor industry has failed catastrophically, where the blame lies with blatant corruption in the form of numerous “zombie fabs”, SMIC’s (Semiconductor Manufacturing International Corporation) outdated fabrication technology
Let’s not mince words: China is playing dirty in the global semiconductor war.
With U.S. export controls tightening and Trump imposing indigestible tariffs paired with Taiwan’s dominance unshaken, and domestic chipmaking ambitions burning through billions in failed “zombie fabs,” Beijing is resorting to cyber-espionage, corporate sabotage, and outright theft to close the gap.
And they’re not being subtle about it.
The Semiconductor Heist: China’s Cyber-Espionage Onslaught
According to cybersecurity firm Proofpoint, a swarm of China-linked hacking groups—with names straight out of a bad spy novel (UNK_FistBump, UNK_DropPitch, UNK_SparkyCarp, and UNK_ColtCentury)—have been caught targeting semiconductor firms, supply chains, and even financial analysts tracking Taiwan’s chip sector.
Their goal? Steal, sabotage, and surveil.
How They’re Doing It
- UNK_ColtCentury (aka TAG-100 or Storm-2077) built rapport with targets before deploying Spark, a custom remote access trojan (RAT).
- UNK_FistBump hijacked Taiwanese university email accounts, posing as job seekers to deliver malicious PDF resumes loaded with Cobalt Strike beacons or Voldemort, a backdoor linked to 70+ past breaches.
- UNK_DropPitch impersonated a fake investment firm, tricking analysts into downloading malicious ZIP files that installed HealthKick backdoors.
- UNK_SparkyCarp sent fake security alerts (e.g., “Your account is compromised!”) to phishing sites like accshieldportal[.]com, stealing credentials.
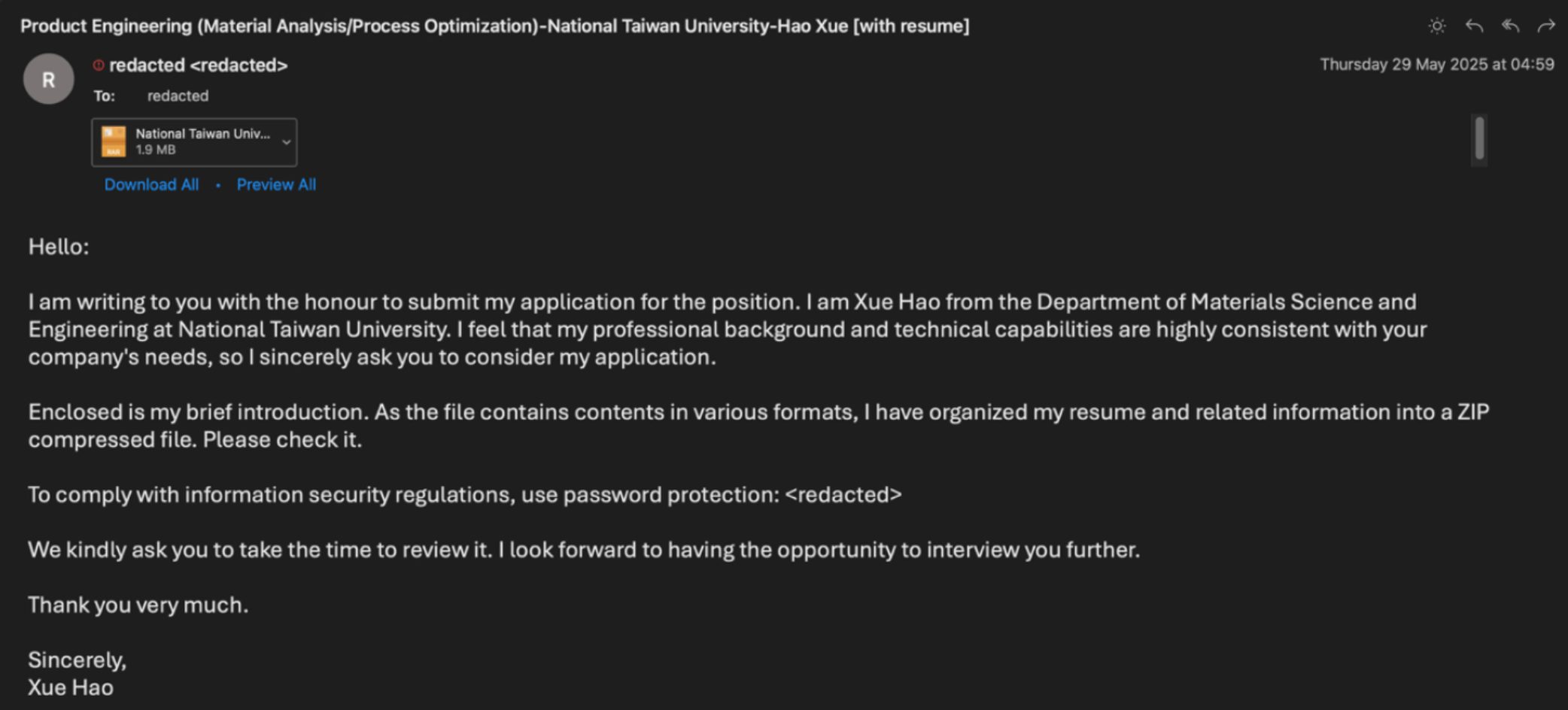
At least 15–20 organizations were hit, from mid-sized suppliers to major global enterprises—including financial analysts at a U.S.-based international bank.
Why Taiwan’s Chip Industry Is In The Crosshairs
Taiwan’s semiconductor sector isn’t just important—it’s the backbone of global tech.
- TSMC manufactures 90% of the world’s advanced chips.
- MediaTek, UMC, Nanya, and RealTek dominate key niches.
When Reuters reached out, none of these firms would comment on whether they’d been breached.
But Proofpoint’s Mark Kelly confirmed:
The motive was most likely espionage.
The Supply Chain Weak Spot
Smaller suppliers—chemical firms, logistics providers, consultants—are the soft underbelly of the semiconductor industry.
- In June 2025, a China-linked group Amoeba attacked a critical chemical supplier to TSMC.
- TeamT5, a Taiwanese cybersecurity firm, warned of rising email-based threats targeting peripheral players.
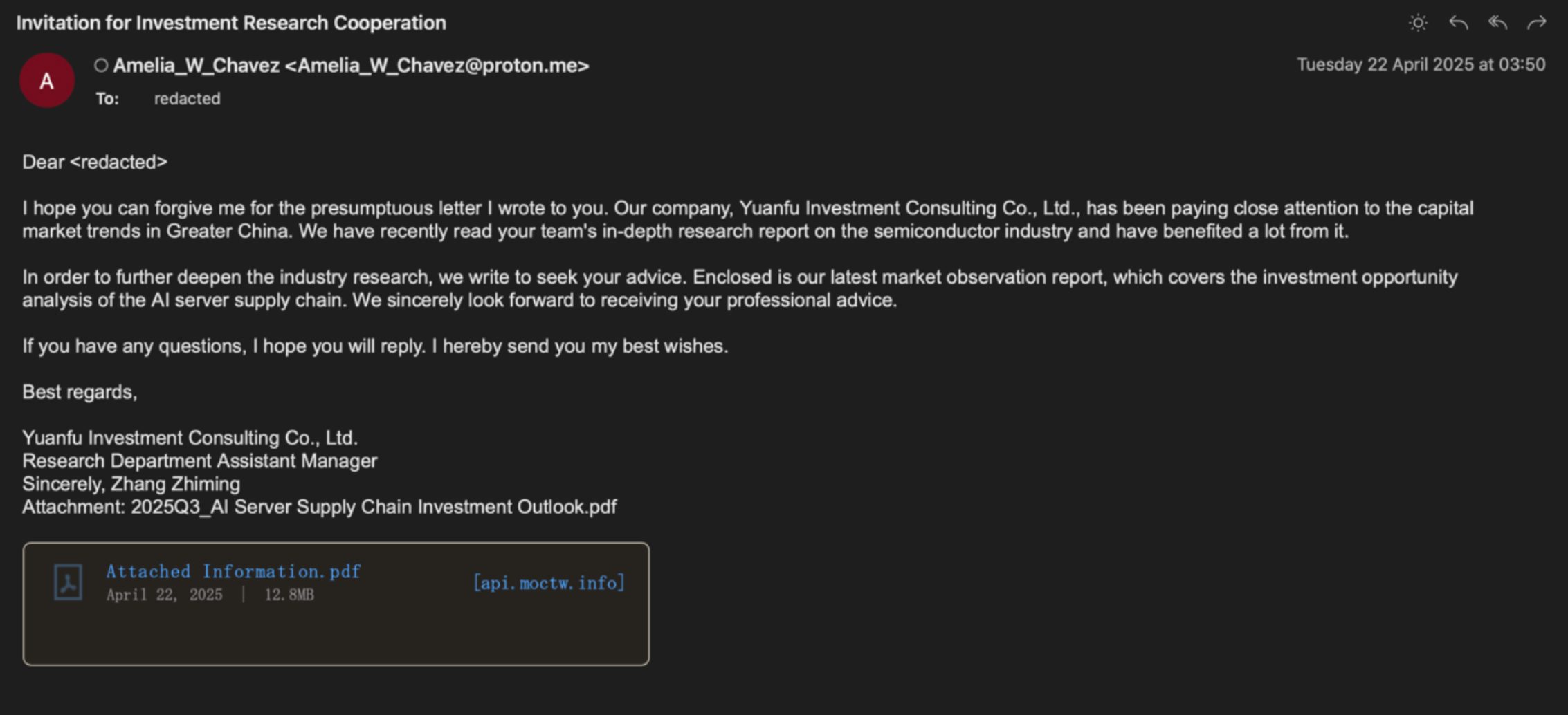
Hack the weak link, compromise the chain.
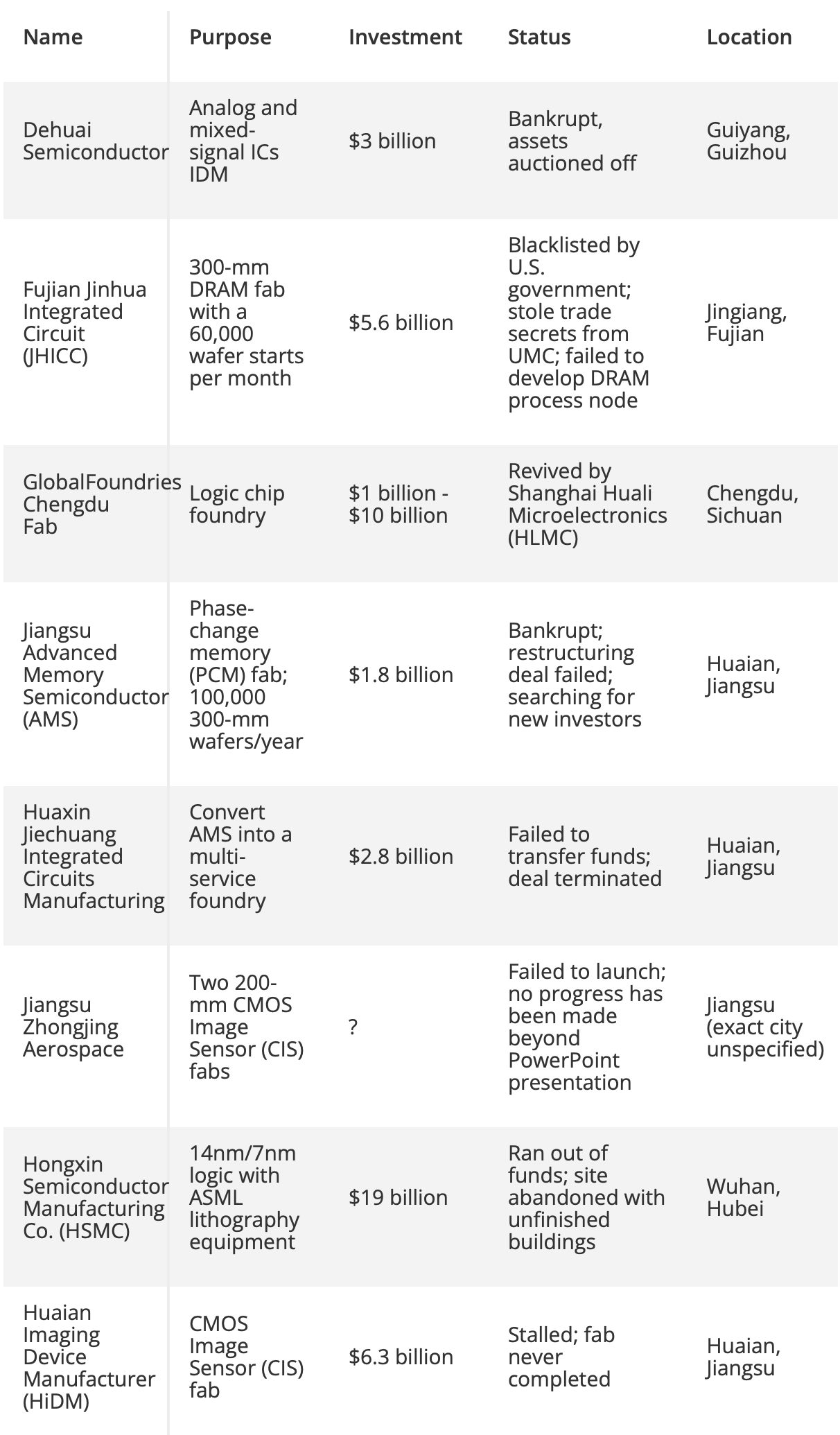
China’s Desperation: A Semiconductor Industry In Shambles
Beijing’s $150 billion push for self-sufficiency has been a disaster:
- “Zombie fabs”—half-built, abandoned factories—litter the landscape.
- SMIC’s 5nm fabrication attempts are lagging TSMC by 4+ years.
- Export bans on ASML’s (Advanced Semiconductor Materials Lithography) EUV (Extreme Ultraviolet) machines are crippling progress.
The Rare Earth Gambit
In a rare “carrot” move, China eased rare earth export restrictions to lure European semiconductor firms.
But let’s be real—it’s a trap.
Control the materials, control the industry.
China’s controlling mindset can be proven by the fact that the superpower just recently imposed a six-month limit on the rare earth export licenses granted to Chinese organizations, effectively weaponizing its leverage over global supply chains, and of course, the U.S.A’s in particular.
The U.S. Isn’t Safe Either
China’s cyber-campaigns are global:
- U.S. Treasury hacked (targeting sanctions committees). What’s ironic is that this happened shortly after the U.S. office imposed sanctions on a Chinese company for alleged cyberattacks. Coincidental? I don’t think so.
- Guam’s infrastructure probed (a strategic U.S. military hub). Guam represents a key U.S. military outpost, i.e., a foothold on one of the remote Mariana Islands in the Pacific Ocean. China’s alleged operation nicknamed “Volt Typhoon” intends to disrupt military and civilian operations in the event of a conflict over Taiwan by mimicking legitimate users to gain control over vital infrastructure, such as water systems, power grids, and communication networks.
- NXP Europe breached (chip designs stolen after going undetected for more than 2 years).
When confronted, China’s embassy gave the usual “We oppose cybercrime” lip service.
Meanwhile, Chinese hackers keep phishing, breaching, and stealing.
The Bottom Line: This Is Economic Warfare
China isn’t just playing catch-up—it’s waging a shadow war.
✅ Cyber-espionage (stealing IPs, i.e., Intellectual Property from TSMC, NXP, and financial analysts).
✅ Supply chain attacks (targeting weak suppliers).
✅ Geopolitical pressure (hacking Guam, U.S. Treasury).
Global Semiconductor Industry: What’s Next?
- More breaches (smaller firms = easier targets).
- Stricter U.S. export controls (choking China’s tech growth).
- Taiwan doubling down on security (or facing collapse).
One thing’s clear: China will get its chips—by hook or by crook.
The only question is, who’s next on their hit list? 🚨
Thank you! Please share your positive feedback. 🔋
How could we improve this post? Please Help us. 😔
[Wiki Editor]
Ali Rashid Khan is an avid gamer, hardware enthusiast, photographer, and devoted litterateur with a period of experience spanning more than 14 years. Sporting a specialization with regards to the latest tech in flagship phones, gaming laptops, and top-of-the-line PCs, Ali is known for consistently presenting the most detailed objective perspective on all types of gaming products, ranging from the Best Motherboards, CPU Coolers, RAM kits, GPUs, and PSUs amongst numerous other peripherals. When he’s not busy writing, you’ll find Ali meddling with mechanical keyboards, indulging in vehicular racing, or professionally competing worldwide with fellow mind-sport athletes in Scrabble. Currently speaking, Ali’s about to complete his Bachelor’s in Business Administration from Bahria University Karachi Campus.
Get In Touch: alirashid@tech4gamers.com




